Most retired equipment is ground up for minimal financial and recycling return…
…that model is financially, environmentally, and socially unsustainable.
The way we all do business is changing. Increasing numbers of staff work flexibly and use their own kit. Corporate smart device and cloud use has exploded. As a result your desktop and server estate is shrinking, and your new asset stock is easier to lose, has a shorter life, and boasts hods of storage…trends that won’t be slowing any time soon. That means it’s time to re-examine your IT Asset Disposal policy. Time to see if you can break the ITAD Vicious Cycle.
NOTE: This post has been produced with permission from Sage Sustainable Electronics (Sage SE). It is based on content previously published in a Sage SE whitepaper. Sage offer secure and environmentally sound IT asset disposal services, including options to recycle and reuse. I originally drafted most of this in 2016 after that long overdue refresher on secure device disposal. References have been checked, but other newer references might be available.
Secure IT Asset Disposal: things are changing
The way we all do business is changing. More and more staff will work remotely (making a bigger portion of desktop equipment obsolete). Bring your own and corporate smart device usage is increasing dramatically, most IT estate maintenance is outsourced, and storage on end-user devices is snowballing. Then there’s the Internet of storage hungry Things. An impending perfect storm…
- New shorter life devices
- More end of life devices
- More data stored in more locations
..signalling the need to re-examine your IT Asset Disposal policy
- Reassess costs
- Explore equipment reuse and resale
- Understand social and environmental factors that are driving the need for a change.
- Confirm that you can still minimise data security risks.
Data can never be fully erased
The tension this causes between IT asset managers and security professionals, creates an ITAD vicious cycle. To date there has been little motivation to rock the ‘destroy all disks’ boat, but now, I argue, it’s time.
Businesses should be managing their risks not building policies around unfounded statements.
This post re-explores the risk of data being retrieved from retired devices. It also examines some of the cost, environmental, and social arguments for switching from Destroy and Recycle, to Refurbish, Repair, Resell, and Reuse.
The ITAD Cycle: why is it vicious?
IT teams will almost invariably have responsibility for managing retirement of IT assets, but the disposal method is usually dictated by security. This relationship is the hub around which ITAD challenges cycle.

Device procurement and use has fundamentally changed (bigger end user storage, shorter upgrade cycle, less in-house server-side, fewer desktops, more mobile devices) so why haven’t ITAD policies changed?
- Security risk aversion – There is a disproportionate belief that destruction of hard drives and other storage media is the only way to adequately mitigate the risk of data disclosure or theft.
- Immature data governance – Data governance at most firms is still relatively immature. It is therefore hard to confirm, with a high degree of confidence, whether retired devices will or won’t contain personal, company confidential, or secret data. IT teams will therefore follow the security path of least resistance.
- Lack of motivation to rock the boat – This has gone on for so long the budgetary burden of storage, destruction, and device recycling just feels (to everyone) like a cost of doing business.
- The consumer driven ITAD market – Most of the ITAD market, led by consumers, aims to destroy and recycle kit as quickly and cheaply as possible. There is little motivation to provide more financially, environmentally, and socially sustainable alternatives.
Alternatives are out there. Alternatives that allow you to recover a significant portion of the depreciated cost of retired equipment, while effectively controlling data related risks, and limiting the amount of material that just ends up in landfill, but ability to take advantage of that does depend significantly on your own asset management and disposal due diligence.
Why co-operate to break the cycle?
This impasse is primarily about data security. After all, as we said before…
…data can never be fully erased
The inevitable image conjured is a CSI Cyber-like scene. The bad guys scrambling to securely wipe their disks while the feds batter down their door. Then, back at the lab, after a bit of cyber jiggery-pokery, all of the deleted data magically reassembles before the agent’s eyes. The only reasonable mitigation for the 1337est crims? Acid baths, drilling drives, or setting it all on fire.

Copyright : Weerapat Kiatdumrong
It is a tough thing to counter, especially when the ‘default to destroy’ policy guarantees that all data, along with reusable kit, is gone. Why would overburdened IT and security professionals dedicate time to researching this with a view to reconsidering?
The fact that your firm likely doesn’t have the same risk profile as an activist trying to hack the NSA is one point, but there are a bunch of other more mundane reasons to invest time in researching alternatives:
3 Big reasons to reuse and resell:
- Money – Refurbishing, repairing, reusing, and reselling retired devices can slice up to 30% off an annual ITAD bill if all you do now is destroy and recycle.
- The Environment – Equipment ending up in landfill, or being part recycled (not much is) adds up to a shocking waste of reusable materials and is environmentally irresponsible.
- Social Responsibilityy – Recycling is a dirty and increasingly difficult job. Worker conditions and pay are serious ongoing concerns, especially with decreasing returns putting pressure on paymasters.
Risk reality vs historical justification
So, first things first, let’s tackle the “Data can never be fully erased” statement. Primarily it is just that, a statement…and a debatable one. Businesses need to manage risks to keep them within a reasonable risk appetite, not build policy around loudest concerned voices.
No-one ever solved a problem without defining it first, so here we go:
The device resale or reuse risk articulated:

Theft of, or access to data on erased devices
Let’s say, for the sake of argument, even best attempts at overwriting data on storage devices leave remnants behind. Remnants that may, if the digital puzzle pieces can be put back together, reveal some personal, company confidential, or secret information. Here are two key data theft incident scenarios to consider:
- Opportunistic data theft – A malicious actor randomly acquiring lots of old kit, or having a rummage around in devices they happen to lay their hands on, in the hope that one or more of them will reveal some useful data.
- Targeted data theft – A malicious actor targeting an ITAD firm and stealing drives or devices because they have confirmed that drives contained personal, company confidential, or secret data.
Pivoting to look at probability, you MAY have a problem on your hands IF:
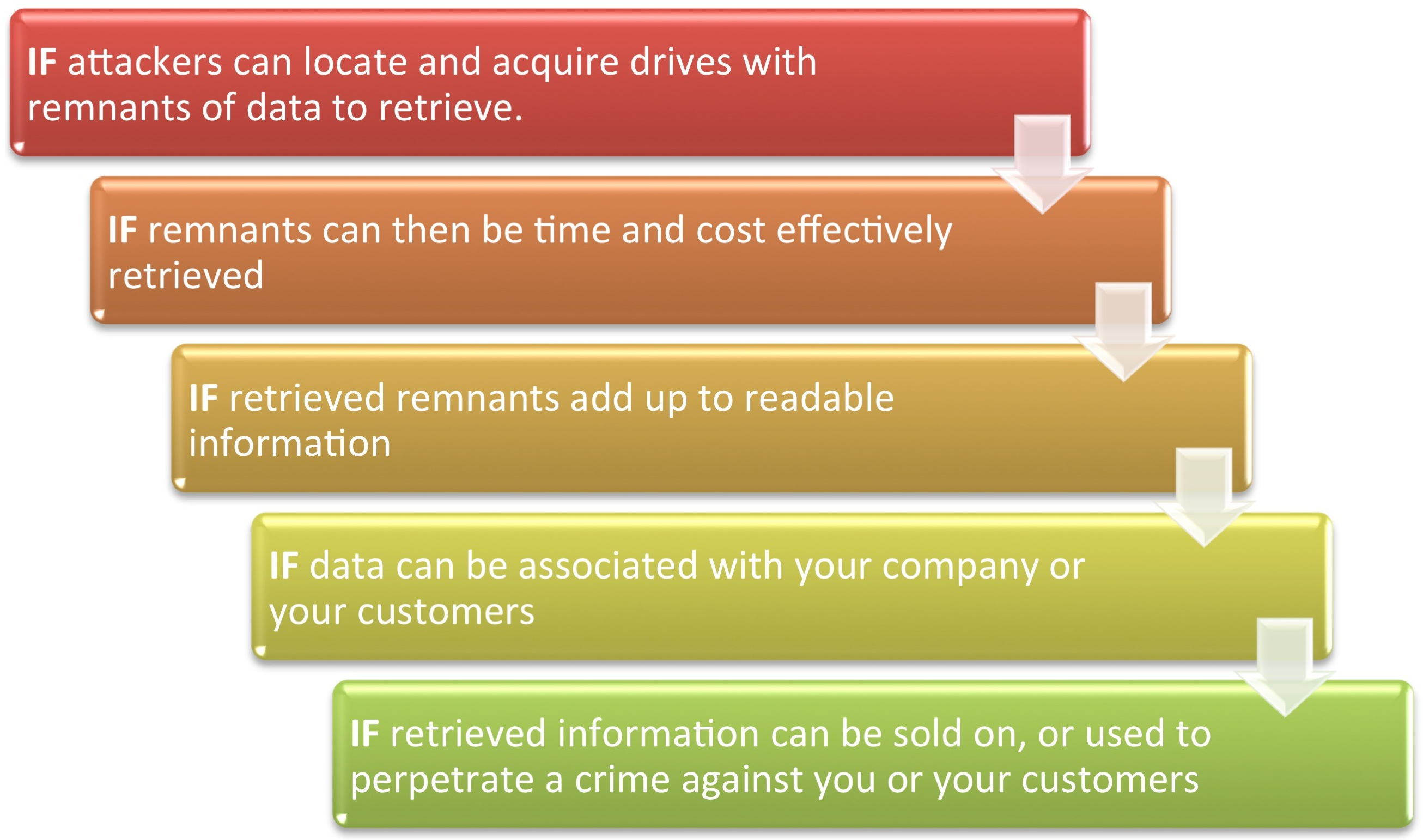
That’s a lot of ‘IF’s
When calculating the probability of a number of consecutive dependent events, you estimate the probability of the first event (often as 1 in Xyrs. or 0.X events in 1yr). Then reduce the overall likelihood of incidents by multiplying by the probability of all subsequent events.
It doesn’t take a statistician to work out how extremely unlikely it is that all of the above factors will fall in the targeted attacker’s favor. How likely is it that A. they can get hold of something readable and B. they can then use that data to cause anyone any real impact.
But those are not the only scenarios.
Theft of, or access to data on pre-erasure devices
This is the key risk around IT Asset Disposal: losing track of assets that are yet to be erased. This is is what persuaded me to publish the post after all this time. Asset management and other vulnerabilities exploited by threat actors to cause this kind of fallout:
NCIX DATA BREACH – Millions of Canadian and American consumers are now at risk thanks to a series of shady backroom deals that have resulted in records detailing 15 years of business being sold.
Travis Doering, Privacy Fly – 9/18/2018, 9:32 PM
A tale of kit liberated from a bankrupted rightful owner by a third-party and sold to the highest bidder. Kit holding LOTS of data and with an exploitable connection to other available machines. Kit that came to the person posing as buyer complete with a set of valid admin credentials. In this scenario, as any security pro worth their salt will tell you, all bets are off. You just buckle up for the incident management ride.
Defining the scenario:
Setting aside that brutal example of what can go wrong and what we all have to lose, this very basically defines the scenario to try and explore risk management and mitigation.
- Opportunist or Targeted data theft from pre-erasure devices – An opportunist, career criminal, or member of ITAD staff, obtains drives or devices BEFORE they have been securely erased or destroyed. If the data is unencrypted, intact, valuable, and attributable, it may enable malicious actors to perpetrate a data related crime, or otherwise disadvantage or threaten the ITAD company, you or your customers with a damaging leak. Even in absence of exploitation, discovery of the breach may result in significant financial penalties or other sanctions from regulators, or potentially impacted parties.
This is not just a resale and reuse risk. It is a risk for all data processing and disposal operations. Kit needs to stay where it’s put in your data centre, or wherever you outsource hosting. It then needs to get safely from its operational origin, to wherever it goes to be decommissioned, then from that location to an ITAD provider, and remain secure until kit is destroyed or data securely erased.
What is the mitigation?
- Your asset management both in-house and by third parties.
- Your due diligence when selecting 3rd party data processors and ITAD providers. How well is your chosen ITAD provider doing? How robustly and consistently are they implementing controls that make reuse and resale of retired kit an acceptable risk?
- The provider’s information security, physical security, business continuity, and disaster recovery controls. Especially staff security, network security, system security,access security, and asset management controls.
- The same controls for any subcontractors used by your third parties and the ITAD provider.
What, in broad terms, is ITAD good practice?
NOTE: As mentioned at the start, this post was originally drafted in 2016. Links have been checked, but some more up to date sources might be available.
Data Erasure
ITAD companies should erase data to Department of Defence (or UK Ministry of Defence) standards. The most common broader standard adhered to is NIST 800-88 (revised in 2014). The most common practice is overwriting data on every drive sector one or more times. If sector by sector overwrite verification shows issues, further overwrites should be carried out. If that fails other methods can be tried. Destroying a drive need only be by exception. Blancco systems are generally recognised as the gold-standard for automated erasure as they exceed all government and private sector requirements.
Solid State Drives (SSDs)
A few years ago this mainly applied to flash or ‘thumb’ drives, but smartphones tablets and ultra-thin laptops have dramatically increased the use of high-capacity SSDs. As for HDDs, all sectors are overwritten and individually verified as being unreadable. Exceptions do still happen. If a sector overwrite fails after multiple attempts, the next most likely steps are hardware layer or cryptographic erasure. The latter involves deleting encryption keys stored on encrypted drives, along with content.
Other storage
What many people forget are the peripheral devices that have a storage capability including printers and copiers. It won’t stop there. On-board storage on these ‘Things’ can be wiped in the ways described above…if clients remember to ask their ITAD vendor to deal with them.
Bad Press for Solid State Storage Erasure
Let’s be honest, SSD erasure has had some bad press, notably this 2011 research paper. It called out erasure failings, but mainly using tools shipped with devices and other wiping means on the open market. They called out problems finding and removing traces of files that had been selectively deleted from disks. It comes down to how SSDs write to disk. Data gets stored electronically rather than magnetically and it is written and moved around in a far less structured way. This can leave ‘remnants’ throughout the drive. Full disk overwriting also came under fire, but less so.
But Things Change…
SDD technology is still evolving, but, as with historical evolution of HDDs the trend is towards making data easier to reliably locate (and therefore erase) and it has been 7 years since that paper was written. A lot can change in 7 years, especially in the world of technology. In 2013 Blancco released it’s new automated SSD erasure solution. It has been verified as leaving no trace of confidential data under deeply invasive laboratory tests. This is not promoting Blancco, it is just a way to underline that problems do get solved and things move on. If doing your own assessment of risks, by all means dig for more recent validated tests of deletion adequacy.
Destruction
Destruction happens under very similar process and control circumstances to erasure. A variety of methods may be used. Shredding is the most common with careful verification that destruction has reduced the drive to a state where individual pieces cannot be put back together to enable data to be reconstituted. That verification plus careful asset management are the crux of good control.
Recycling
By the most generally accepted definition this conjures up an overwhelmingly positive feeling. Taking potential landfill and retrieving useful components and raw materials. Things that can be given a new life and at the same time take pressure off dwindling natural resources.
Financial return from recycling is also a fundamental part of ITAD firm revenue, but how socially and environmentally sound is it?
Environmental and social considerations
Reputable firms should not incinerate e-waste or dump it. Air pollution or ground and water pollution from degrading components, can have a significant environmental impact over hundreds of years. Those things are outlawed in the main, but US state laws can vary significantly. The vast majority of firms won’t contravene these laws because of either ethics or the threat of sanctions, but the motivation to sidestep controls is significant.
There are international laws in place to prevent companies taking advantage of cheap and vulnerable overseas workers including children and prisoners. The Basel Convention, an international treaty under the United Nations, forbids the trade in toxic materials, including e- waste, between developed and developing countries.
There are many competing reasons for less reputable firms to bend or break laws. Laws that are applied variably across US states permitting more leeway than is granted to the vast majority of other countries. These are the two key independent regulatory hooks for international IT asset disposal.
The E-Stewards programme and R2

Extended Producer Responsibility
ERP programmes (here is an overview from the OECD) are another pillar of intended defense against an unsustainable ITAD world. The concept is to require producers to shoulder a fair proportion of the eventual disposal burden to encourage the right sustainable and recyclable design considerations and investment in efficient disposal mechanisms. Needless to say that hasn’t, especially in the US, been the case. Instead the producer contribution has been minimised as far as possible, especially by the biggest firms, with the remaining burden handed over to consumers through increased prices. Here’s more on that from Sage SE’s blog
Capital equipment investment
High throughput recyclers (as opposed to smaller shops who might spend significant time extracting parts that have a good resale/reuse value) will have invested millions in infrastructure that quickly breaks kit into raw material and waste. Materials, including precious metals that they have to pay other firms to recover, further squeezing margins.
Having bet the farm on this business model they have little motivation to differentiate between kit destined to be ground up and kit that could return significantly more value to clients while reduce unusable waste. An idle recycling machine costs money and customers are not pushing for things to change.
Rapid firm failure due to high competition and low margins
Another key consideration is the viability of ITAD companies. With that big capital investment in high-throughput recycling equipment, or the effort overhead for small shops who painstakingly recover reusable materials, many firms don’t last long. That often results in stockpiles of kit being left in storage units. There are also plenty of examples of firms liquidating and reinventing themselves, leaving pre-existing customers struggling to get legal recourse or kit returned, a risk no-one should underestimate.d
None of that encourages R&D…but all of it is a driver to find cheaper or even legally questionable ways to make ends meet.
How do we manage the risks?
Asset Management
Most data goes missing or falls into the wrong hands because companies fail to keep track of it. Off-network data can be a particular weak spot. You, your 3rd party data processors, and ITAD companies should have policies, robust procedures, and scrupulous record keeping around all of the following:
- Safe transport
- Safe storage
- Unique asset identification
- Evidence collection and retention to prove an unbroken chain of asset custody
- Processes controlling unauthorised outside or insider access to asset inventories,workflow logs and physical areas.
- Monitoring for exceptions and anomalies in asset inventory contents, workflow records and physical/system access logs.
As with most risks, device loss or theft gets harder to prevent the more motivated and expert the attacker. There should be robust and well-practiced incident response plans for common device loss or theft scenarios, but cost/benefit for protective and detective controls is down to the relative risk of loss, theft, or misuse in a given situation, and the balance you have to strike with getting your job done.
All the hosting locations I’ve been to stop just short of a strip search, there’s a camera every 10 paces, mantraps between you and the cages, and every visit requires 24 hour notice with photo ID. You would expect something similar for an ITAD provider’s pre-erasure kit stores, but you can’t enforce that for every area of offices despite the fact you could scoop a few phones or laptops after a single circuit. Do you effectively compensate for that residual risk?
Supplier selection and due diligence
If you have flexible ethics and huge legal indemnity insurance it is ok to pick the first ITAD firm that ranks well on Google. Otherwise, a big part of supplier selection should be ensuring they adhere to one or more industry standards for responsible practice and have a sustainable business model that offers alternatives to recycling. That’s aside from more general due diligence around their financial health as a firm, their data protection capabilities, and the state of their security control. As regards social responsibility, the most stringent regulations that companies can chose to adhere to are the ones mentioned before:
- E-Stewards – The Basel Action Network website. BAN created the E-Stewardship programme.
- R2 – Sustainable Electronics Recycling Internationald. SERI oversee standards and certification for R2.
Ongoing supplier governance
Like any other supplier that handles your data, you should establish a good relationship, foster trust, but then verify how well they have implemented and are running controls. Assess the inherent risk they can cause your business, then decide on appropriate governance. Given the ITAD business model, you might want to rethink how vendor governance work is scoped if they don’t come out as priority to look at.
Due diligence and regular ongoing assessments should not just focus on erasure and recycling methods. Look at all layered controls that can influence security of your assets. In particular the on-going effectiveness of all the asset management controls listed above.
Things will go wrong. No process or system is 100% reliable. It is not about incidents happening (unless there is a concerning trend), it is about how they are dealt with. You need to state in contracts that ITAD vendors must notify you promptly and have a robust incident response plan in place. Their ability to quickly and effectively investigate and mitigate impact any impact on you depends enormously on robustness of the aforementioned asset management controls.
Data Governance
If you are now convinced that destruction is not the only way, you may still want a belt and braces approach to your most sensitive data. The problem: most firms do not have an adequate handle on where it is, or even what it is.
Structured Data
- Sensory Data – GPS data, manufacturing sensors, medical devices
- Point-of-Sale Data – Credit card information, location of sale, product information
- Call Records – Time of call, caller and recipient information
- Data in Logs – Webserver, application, firewall logs
- Application Data – Anything input by users into defined fields e.g. personal data,sales data, bank account information.
Unstructured Data
Using email as an example. There are certain values that would fit into a table. Sender, recipient, etc. It’s the message itself that’s unstructured. You could have a column for it, but with basic data analysis tools, it would be useless. Other examples are:
- Word Doc’s, PDF’s and Other Text
- Audio Files – Customer service recordings, voicemails, 911 phone calls
- Presentations – PowerPoints, SlideShares
- Videos
- Images
- Messaging – Instant messages, text messages
Tackling immature data governance
Say your new policy states that disks containing secret data and sensitive personal data must be excluded from your plan to do more reusing and reselling (in my opinion, if you have to exclude something, a very rational line to draw). Focus effort to improve data governance and tracking on that information and in the process mitigate a lot of risk quickly. Users and storage locations for this data should be naturally limited, so it is a good starting point.
No-one will ever be able to confirm with 100% confidence that all storage media and devices have NO confidential, secret data, or sensitive data on them to start with (think about the hugely varied and rapidly changing contents of your inbox). But residual risks, if using diligent ITAD firms, should still be well within tolerable levels for the vast majority of firms.
Managing BYOD data risks
The challenge of keeping company data safe then erasing it from BYOD kit is the subject of much debate. More and more companies allow users to replace corporate equipment with their own devices subject to network access controls and encryption, but shadow BYOD (users working on their own devices regardless of company device use policies), happens to everyone, and the risk is only going to get bigger.
Putting day to day risks aside, when those devices reach end of life (something they do often if the amount of phones in my drawer is anything to go by) firms could take advantage of an ITAD provider who refurbishes, repairs, and resells. Stop old devices getting lost, going to dangerously tech savvy offspring, getting disposed of insecurely, or being sold to ‘we buy any phone’ type outfits. You could afford to incentivise staff to do so if, like Sage, they cost services allowing for value you can recoup. Worth considering before someone switches off remote wipe, turns off the pesky pin protection, and misplaces the succession plans you emailed to their auto logged-on Outlook Web Access, or photos of that whiteboard from the merger negotiation.
The Business Case
The more equipment you refurbish, repair, resell and reuse, the more money you will save and the more you will fulfil your social and environmental responsibilities. But it has to be affordable and it has to manage your risks. If you can’t stay in business, or suffer frequent breaches no-one wins. A key challenge is understanding the real market value of your retiring assets, broken or or not. Its the most obvious foundation for your business case. The reason to question how things have always been done.
Sage SE, the firm who asked me to write the original version of this post, put their Blue Book together to fill this gap (other similarish resources exist, I am not recommending this one to the exclusion of others, yada yada). Yes, you could alternatively check out price lists for smartphone trade-in companies, people marketing kit on eBay, or trawl some darker web price lists, but it would likely drive you nuts to try and accumulate the same kind of information.
Information on assets is roughly equivalent to a trade car price guide. Differentiating on the basis of type, age and state of repair. It gives you that means to compare ITAD options in a meaningful financial way:
Value
- Refurbished
- Grade A
- Grade B
- Parts or Sale After Repair
Cost Models
- Reusable Yield – Percentage of total retirements reused/resold versus recycled.
- Procurement Avoidance – Cost difference between refurbishing and redeploying assets and the expense of buying new ones.
- Average Selling Price – Total revenue divided by the number of items sold per asset type
Concluding
Is all of this sufficient justification to change your default device destruction policy? Not convinced? How about justification to spend time doing some research given the potential to make a substantial difference on so many fronts? Maybe just take the first few steps:
1. Break the current impasse between IT asset managers, procurement, and security
Get round a table and use a risk framework like FAIR (Factor Analysis of Information Risk), something that deals in annual loss expectancies, to really drill into those data security and data protection risks for device refurbishment and resale or reuse.
2. Check control you currently have over your crown jewels
Do you have a reliable record of data processing that at least covers your most secret, sensitive and most at risk data assets? Ditto for the devices that hold it? Have you maintained that control when data is shared with 3rd parties? What about when those third parties go boom? Are data/device return, data device/deletion and/or data/device escrow exit controls in place with suitable liability for any breach?
3. Review your current contracts with your ITAD providers
If there has been no assessment of ITAD supplier financial health, security, and data protection in the past 12 months, do one. Reassess the amount of devices likely to be retired and fundamentally kick the tyres of their costed options versus competitors offering more environmentally sustainable alternatives. Just like for other data processors, are those exit and contract breach controls in place to insulate you from fallout if they cease to trade while still in possession of your equipment?
4. Cast your eyes to the IT asset horizon.
Where are device trends taking you? In exchange for your old world of hosted tin and desktops, how well can you control the new world of terabyte smart things and the IoT. That, if nothing else, deserves a once over your IT disposal strategy, don’t you agree?