Maria Korolov, writing for CIO Online, summarised key findings from (ISC)2’s recent report on Women In Security. A report informed by the their 2015 Global Information Security Workforce Study.
The standout figure? Only 10% of information security professionals are female. A decrease of 1% since 2013 (failure to keep pace with workforce growth rather than a drop in absolute numbers), and far lower than the 15% I had historically accepted as a shocking baseline.

P2 (ISC)2 Women In Security: Wisely Positioned For The Future of InfoSec
Also, when found in senior management, they are more likely to be highly educated, older, and less well represented in the highest salary brackets.
Are the GRC figures accurate?
Jan Winter rightly pointed out that there are many different flavours of GRC, and most of them have a broader remit than just security. For instance; operational risk areas typically deal with risk linked to all supporting functions (e.g. HR, Marketing, IT). That doesn’t mean practitioners shouldn’t be considered security professionals, but there is a big distinction between a pro who has security on a list of teams to call for regular inputs to more general GRC forums/assessments/reports, and someone solely focused on, or specifically experienced and trained to deal with security GRC.
Is this about women leaning away from the tech coalface?
A dangerous question wrapped in an assumption, as suggested by my comments about the umbrella GRC term. Specialist security GRC roles are not just about ‘soft skills’ (gosh I dislike that phrase).

What’s notoriously elusive is a useful definition of GRC in our security context. It should not be confused with the big bits of software sold to manage related data and produce reports (David Froud with a succinct look at that). Tools don’t work without accurate data, intelligent programming and locally relevant configuration. Intelligence informed by the real job of defining, assessing, categorising, aggregating, and wrangling security related risks (a mammoth challenge we’re still struggling with), working to rationally comply with laws, regulations and policies, and putting a governing wrapper around all that.
We need models to normalise data produced manually and by tools. Working to ensure outputs properly represent the matrix relationship between risk indicators, assets, and interrelated tech, processes, people potentially impacted. That, by most yardsticks, is a Data Science role. One of the highest profile and conceptually most technical roles in the trade today. And, if you read the source article a little more carefully, that’s where women are specifically better represented – Good news!
Then there are those ‘soft skills’. Ironically the hardest part of the security job. At base, making sure non-specialists can make better and more ethically balanced business decisions. To do that they have to integrate consideration of security into defining and aiming to achieve business objectives. Balancing improvements needed against other priorities. GRC paints, manages and promotes visibility of that picture. Get that wrong (perhaps misreport priorities) and security heads in the wrong breach-inviting direction, or non-GRC security peers can find themselves out of work.
Potential future questions?
- Is the GRC role dedicated to security?
- Have you had any security specific experience or training to help you perform your GRC role?
- What skills make up your main role: Data Science? Stakeholder Management, Risk Assessment, Compliance Management…etc etc.
Regardless of the breakdown, the more the merrier. Every woman exposed to security realities, discussing them with non-security peers, taking discussions home, and generally raising security’s profile is a good thing.
Is GRC just less exciting?
Taking a breath, and dealing again with common perceptions of GRC, this is where things get ticklish. Women and men often tread on eggshells, unwilling to stereotype and demonise anyone. There’s also always awareness that a current or future employer may be watching. However, some meaningful suggestions were shared:
There was a general feeling that the sometimes combative and uncertain tone of coalface security (defending the castle, nailing the bad guys, assuming you’ve been hacked, innovating to protect, navigating the dark spaces of the internet), struck more of a chord with men than women. Or that the perception and less technical aspects of GRC roles (e.g. pulling insights together, injecting coherent, repeatable oversight, finding patterns, improving communication, negotiating, conflict resolution) played to strengths typically associated with women. And those people are not alone. Those themes and many others here are mirrored in this article by Jen Weedon (@jenrweedon – Formerly at Mandiant/FireEye, now an independent cyber threat intelligence expert)
For gender diversity in cybersecurity, fix the image problem
Potential future questions?
- Qualitative questions about why women chose to aim for security GRC rather than tech, or why those already in the trade move between tech and GRC.
What the heck do I mean by ‘tech’?
Time to talk about what I mean by that mega-umbrella term ‘tech’. This doesn’t have a pretty definition. In the context of this article, it’s a distinction between GRC, other security processes, security people management, and everything else InfoSec (a partially spurious distiction given aforementioned points about technical components of GRC, plus the fact tech doesn’t happen as if by magic. There are a hugely underestimated number of processes, people inputs, and non-technical risks to tackle to make tech useful).
A definitive list of roles outside GRC? Impossible right now, although Lesley Carhart (@hacks4pancakes) has done an incredible starter for 10 on her blog. There will be more valuable diversity insights if we do more of that, and get better at defining what makes us good at roles. We’ve struggled because it keeps evolving, and responsibilities can be split 100 ways, each way easily constituting a full-time job with distinctive skills. By contrast, in smaller firms, all that can coalesce round a couple of blokes employed to ‘do security’.
I’m an example of that multiplicity. Like many others, I started late then bounced around before ‘falling’ into security (my early background was a business degree, customer services, IT support, desktop and network engineering, then consulting on network security, identity and access solutions). That evolved, via a number of corporate ITSec and InfoSec roles, into GRC, because I was driven to better represent the work and outputs of my peers.
Would I have taken a more direct route had the opportunity arisen? Maybe, but I do remember feeling IT and security was the preserve of boys who started to code before their voices broke. A world I assumed (in the absence of other evidence), I was excluded from before the career choice ever occurred to me…and I’m not alone in that perception. The only reason I’m where I am right now is because an IT helpdesk recruited on potential not experience.
How impactful is a lack female tech role models and peers?

https://twitter.com/InfoSecSherpa/status/661674886591565824
The counterpoint being a number of women at the heart of the hacking world (in terms of skills, not murkily emotive stereotypes), who talked about parents who worked in STEM, and how that normalised being around and working with technology. Yet another complimentary theme was that security wasn’t a first career for many – men and women. Part of that is the relative youth of the industry, but that tweet suggests there may well be more to it.

https://twitter.com/S_Clarke22/status/661646105655025665

On that one simple front, my poll shows a very different picture to Lesley’s data (links to higher res images to come). Her sample included a control group and broke down female respondents into self-identified groups. It’s interesting and provides anecdotal evidence that early exposure to tech via an interested parent/guardian is important.

Beyond that there’s much much more in Lesley’s data still to analyse. My most significant takeaway was the rapid and broad attention paid to her survey (and my poll) by both men and women. Men and women who want to advertise the great work most of us get to do. Something we need to do better to attract girls with security related skills, but perhaps no knowledge of the trade, or doubts about the value they could add.
Potential future questions?
- To all women in tech or GRC: Is security your first career?
- To women for whom tech security is a 2nd, 3rd or 4th career choice: Would you have started sooner had you had more encouragement, an understanding of security as a career choice, or seen peers interested in/working in the trade?
- To women already in tech and GRC (to build on that survey): Going beyond that question about parents working in STEM, to parents interested in STEM. Then a step further to other family members working in/interested in STEM and other STEM related positive influences anywhere along the way e.g. schools, clubs, partners, work colleagues, friends.
- To women considering/working in tech security: What career choices within security are you aware of and what do you think they entail (suspecting there may be a gulf of difference between perception and reality).
Then there’s the more usual go to place for any conversation about women working in notoriously male dominated trades: The pay and conditions discussion.
What, in terms of pay and conditions, attracts and retains women?

P14 (ISC)2 Women In Security: Wisely Positioned For The Future of InfoSec
Backed up by this chart from the same (ISC)2 report.
There is a special kind of dynamic in the security industry. It’s been called the Wild West because it is still young, lacking coherence, and tacking poorly defined risks. That makes space for a kind of creativity and camaraderie you don’t find in many more mature industries.
So, perhaps time to delve a bit deeper into bigger questions about women and work, because more general culture plays a big role too.
Flexible working isn’t a gender-specific debate
The cultural norm for professional work…
- 40-60 weekly hours,
- Hours bridging the middle of the local working day,
- Working in an office
…needs to be be robustly challenged (this was the subject of a mid-degree project of mine, so it isn’t just informed by personal work experience).
BUT, offering non-standard working models backfires if only one group is targeted. Both men and women need flexible working opportunities, and protection against negative impact on perception of their credibility and professional commitment. To do that, change needs to be sponsored at the top. A place where, ironically, people work far more flexibly than most people in the middle ranks. See what Proctor and Gamble did for some inspiring, financially supportable, and achievable ideas.
Modes of work, performance measures (at least tacitly), and pay structures have been geared to that full-time standard for more than a century. A century that began with women having little access to higher education and paid work, and no real control over childbearing.
 Then, in the middle, women were propagandised into technical work (negating any claims they were not capable of doing it) to support the WWII war effort…
Then, in the middle, women were propagandised into technical work (negating any claims they were not capable of doing it) to support the WWII war effort…

…before being propagandised (albeit only partially successfully, as women’s participation in the labour force continued to grow after the war), back into the role of homemakers.
Betty Friedan wrote the Feminine Mystique about that 50s housewife culture – It changed lives, but should be seen in a bigger, more culturally and racially diverse context. Between it and it’s critique there’s good perspective on home life of our parents, and in turn our upbringing.
In the 60’s, in the UK, there were still blocks on working in many professions for married women, and many were forced to give up work when they got married (like my mother, forced to quit work in 1963, when both she and my father worked in banks). The premise: a woman cannot effectively support a household, and enable her husband’s career, if she too is working. A premise made a partially self-fulfilling prophecy by the way work was structured. Now, in our dramatically changed and digitised world, women have equal(ish) access to education and work. The concept of being forced to stay at home (as opposed to doing so as a perfectly reasonable choice), is thankfully alien…at least in my culture.
Backing away from the history lesson (sorry if some feel I’ve gone too far off piste), and recognising that some jobs demand bums on seats during core hours, and people on-call, the presenteeism (gotta be seen at that desk early…and seen to leave late..to get on) needs to stop.
Training and knowledge sharing needs to evolve
Characteristics of many security roles that defeat many women are knowledge acquisition, and skills retention. Few industries evolve as fast as InfoSec. The process of gaining qualifications, and doing necessary research around the job, doesn’t respect the remaining imbalance in non-work responsibilities.
Taking CISSP as an example: Many firms demand courses are studied for in your own time (with or without exams paid for by the firm). Continuing Professional Education (CPE) points have to be obtained on and off the job, often through further training, conference attendance, reading, and teaching. Although gender roles have evolved dramatically, most women between the bottom rung and the boardroom, are likely to have the lion’s share of responsibility for childcare, household management, and eldercare. They also have babies, and naturally spend a little time off work before coming back and/or working less hours after they return.
Putting aside those who attack mothers who work, there are also also people who attack fathers picking up their share of family responsibilities. Again a personal example, but one that very visibly demonstrates what’s no doubt often said behind closed doors. When my partner who worked in a small firm, had to leave to pick up one of our kids who had been hurt at school, the MD’s wife said “Why can’t SHE do it?! I have always worked, and I have never once had to ask my husband to do that!” There’s no need for me to point out all the things wrong with that sentence.
That split of care is evolving, but while my absence to fill these household gaps causes less ructions, I will continue to do more than my fair share. Weathering any impact on my career, and the the fact it makes “own time’ for studying a bit of a myth.
Time to take that into account, because I know I’m far from alone with my experience. Prepare to fund more intensive training, on-site work-hours training, and work-hours knowledge sharing between peers. And please stop (ISC)2 pretending babies don’t happen. That’s a personal plea from me because I chose to take a few months maternity leave, and found out my time to gain CPEs could not be extended if I didn’t find a physician who’d say I was on long-term sick leave.
Working with technology has to be normalised for girls
Next, inspired again by that tweet from @InfoSecSherpa, and similar ones from many others, we need to recognise what’s happening in our specific cultural past.
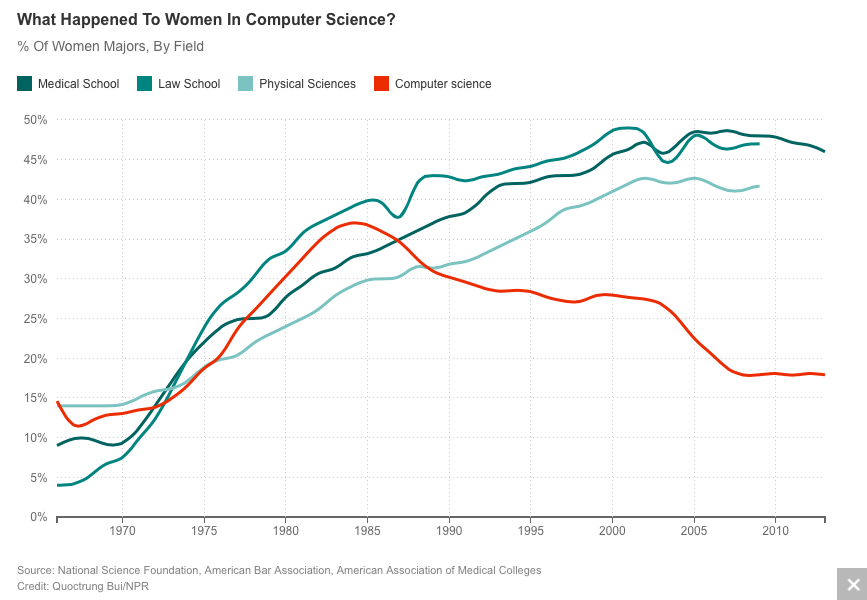
http://www.npr.org/sections/money/2014/10/21/357629765/when-women-stopped-coding
Some fascinating points were raised in that article: When Women Stopped Coding. A quote to illustrate:
This idea that computers are for boys became a narrative. It became the story we told ourselves about the computing revolution. It helped define who geeks were, and it created techie culture
Many initiatives are out there trying to tackle this. Some great ones on the tech front are collected in this article: We All Need More Women Who Can Code by Mark Malmberg on the Nerdery Blog (do point me at others and I’ll be happy to share).
All of which is making a difference, but culture, as everyone knows, is very hard to change. Which made me wonder out loud whether our generation of professionals will still be around when that 10% creeps a meaningful amount closer to 50.
Hitting these challenges head on, many of my female peers are working hard to bring the worlds of technical (and less technical) security to the attention of younger women. Tackling a fundamental ignorance of the range of work in the field. In particular, in my case, to my two daughters. Not pushing them, but putting great applications of tech in front of them. A tech and security awareness raising journey I describe here: Diary of an InfoSec kid – Mindfulness, Moshi Monsters & Minecraft:

https://twitter.com/S_Clarke22/status/661646105655025665
Treading carefully round the stereotypes
Having said that, while doing my bit in the world at large, it can sometimes feel uncomfortable (as Steve Christey Coley intuitively called out in this tweet). I don’t and have never felt forced. That is the wrong term. But I do feel a great weight of responsibility.
Beyond the fact I’m a woman, I don’t claim any special expertise on the subject of diversity. It puts me in a bind because I’ve typically avoided leading with my gender (meritocracy should rule), and I don’t want to misrepresent/stereotype a huge and hugely varied group of people. A feeling I know is shared by other pros called upon to comment.
When all’s said and done, like so many of my peers, I am VERY happy to help when i can add value. The ultimate aim, as I said to Limor Elbaz, is to do myself out of a job:
I’ll know we’ve made progress sorting the lack of gender-diversity in InfoSec, when I stop getting asked to talk about sorting the lack of gender-diversity in InfoSec
Defeating the “need advanced computer skills, to get advanced computing skills” trap
What I would like to see happen, to honour the work being done by many fantastic women and men, is our trade looking harder at itself. Digging into the characteristics that make great security pros of all different flavours. Tapping up our friends in other disciplines, and in the sciences to see how that translates into core aptitudes. Taking the results on tour to all educational establishments. Creating fun, engaging, assessments to identify those aptitudes in mixed, or (if the predominance of guys puts the girls off), gender split groups. Making it something that might happen on computers, but making sure it doesn’t require any advanced computer skills to do.
That “need advanced computer skills, to get advanced computer skills” perception and reality is insidious, but perhaps the antidote is one reliably gender-neutral thing: Delight and pride when you are told you are good at something. We could translate something like I describe above into a way to show girls they CAN do it, they ARE tech able, it ISN’T rocket science, but it IS exciting, and yes, if you test better than the boys, you get bragging rights. Following up with news about career paths opened up, courses for extra credit and mentoring programmes. Perhaps then we would break some barriers for those who didn’t get into computers early, and feed acceptance of gender neutrality.
Is part of the answer encouraging women to consider coding, hacking, GRC (or any other InfoSec related role) as a career change?
So, at the end of this monster post (that has strayed far from the GRC vs Tech topic into bigger questions), how about this idea from Cheryl Biswas (@3ncr1pt3d)?
In Praise of Older Women: [Should we create] opportunities in Security for those with life experience? Why? Because we keep asking why the young girls aren’t going into coding; why the millenials aren’t choosing InfoSec. What about some smart, savvy older women who are sick of being relegated to admin and retail, and really want to do something? Women used to working harder to get what they want, and with great time management skills. We can learn the tech; it’s the aptitude and soft skills that make a difference.
She only suggested it this morning and I’ve had no time to robustly respond, so why don’t you respond for me? I (to start things off) think it’s a cracking idea.
